
Feature Spotlight
MDM Secrets for Trusted Devices
FEATURE
HIGHLIGHTS
FEATURE HIGHLIGHTS
- Control which devices have access to your mobile forms
- Secure your application deployments to trusted devices
- Extend your current MDM program
THE PROBLEM
A common challenge in large, modern IT departments is keeping up with the sheer number and variety of mobile devices attached to corporate networks. The rise of workforce mobility and widespread adoption of BYOD policies create additional security concerns.
IT departments deploying enterprise-wide applications must ensure that only authorized devices deployed in the field have access to corporate applications and the data stored within.
OUR SOLUTION
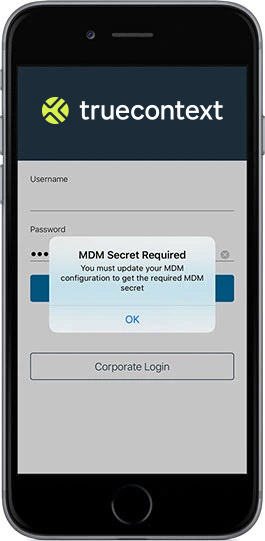
MDM Secrets for Trusted Devices is a team-level feature that provides an additional layer of security for corporate IT departments using MDM.
Enabling an MDM Secret means that end-users can only access the app and corresponding stored content if they are logged into a trusted device, as recognized by your MDM solution. Gain full, granular control over which devices can access deployed forms.
Ready to unleash productivity?
Get a demo and start a trial today.
By submitting this form, you agree to our privacy policy.


